Over the last decade, discussions of online privacy have taken precedence in mainstream media.
Numerous reports of massive surveillance across the globe have brought to attention just how much governments can go to infringe people’s privacy.
Edward Snowden’s expose about federal government surveillance of US and foreign citizens sparked a global conversation and divided Americans, with 44% saying surveillance harmed public interest according to a Pew Research Center survey.
Yet that’s only the tip of the iceberg. Have you heard about the surveillance alliances of governments?
The 5 Eyes, 9 Eyes, and 14 Eyes countries collaborate extensively in surveillance. While the origins of these alliances go back to the 1940s, little is known about how they operate.
What do they do? How much of a threat are they to your privacy? How can you avoid falling victim to their surveillance?
In this article, we’ll go through the 5/9/14 eyes countries in order to establish who’s spying on you Online.
Who are the 5 Eyes Countries?
The Five Eyes (FVEY) is an intelligence alliance consisting of 5 countries; the United States, the United Kingdom, Canada, Australia, and New Zealand.
The 5 Eyes western intelligence alliance was conceived in the Atlantic Charter in 1941, renewed with the passage of the BRUSA agreement in 1943, and officially enacted in 1946.
The original objective of the FVEY was to monitor the Soviet Union and its allies. With time, however, the political landscape changed and the alliance shifted focus to War on Terror.
Today, the alliance shares signal intelligence data among its members in two ways.
Communications Intelligence (COMINT) involves the interception of voice communications as well as emails and text messages.
Electronic Intelligence (ELINT) involves the use of electronic sensors to signals unrelated to communication, for instance, signals from radars and missile systems.

Each of the countries in the alliance has intelligence agencies that spy on people in various parts of the world and share the data with each other.
In fact, this collaboration has enabled unconstitutional surveillance of citizens. Documents leaked but Edward Snowden revealed that the US paid the UK to gather data on US citizens.
Who are the 9 Eyes Countries?
The 9 Eyes is an agreement that consists of members of the 5 Eyes working with Denmark, France, Netherlands, and Norway.
With little information about these groups, it’s considered an arrangement between SIGINT agencies to share intelligence.
Who are the 14 Eyes Countries?
The 14 Eyes refers to the intelligence group consisting of all members of the 9 Eyes in addition to Germany, Belgium, Italy, Sweden, and Spain.
It was formed in 1982 and is an extension of the United Kingdom- United States of America (UKUSA) agreement. It is referred to as the SIGINT Seniors Europe (SSEUR).
Again, the details of this agreement have not been well documented. However, the main agenda of the alliance is to share surveillance information among its intelligence agencies and discuss security issues.
Third-Party Contributors
There are other countries that contribute to the 14 Eyes group. These third-party contributors share with and receive intelligence data from the 14 Eyes but have fewer rights and mandates.
They include Israel, Singapore, South Korea, Iceland, Greece, Hungary, Romania, and other countries.
How the 14 Eyes Countries are a Threat to Your Privacy
The 14 Eyes alliance has great implications for personal privacy.
Intelligence agencies in these countries have great access to personal information through advanced technologies they have developed and the extent of this access is not well known.
Revelations from the Edward Snowden expose make it clear that your online activities and phone conversations are under considerable surveillance.
The 5 Eyes and 14 Eyes countries for instance operate several surveillance systems on a global scale.
The ECHELON which was established in 1971 to intercept communications of the Soviet Union and its allies still operates today. It uses communication satellites to intercept private communications which are then stored for analysis.
PRISM, which was established in 2007 collects private communications data of citizens from major tech corporations like Google and Facebook.
Lastly, the XKeyscore surveillance system lets the National Security Agency NSA read any online communication and identify the location of any smart device.
However, the extent of surveillance doesn’t end there as the 5 Eyes countries have made extra efforts to undermine people’s privacy beyond their jurisdiction.
Snowden’s expose of NSA paying UK’s intelligence agency GCHQ to surveil US citizens is a great example.
The governments have also initiated acts in the constitution to allow greater surveillance of citizens. The USA Patriot Act of 2001, Australia’s Telecommunications Amendment Act of 2015, and the UK Investigatory Powers Act of 2016 are great examples.
While these nations have invested heavily in surveillance for security purposes, they have ignored providing standard safety measures for the threats that could arise due to unlimited access to personal data
5 Eyes Push for An End to Encryption
Recently, lawmakers from the 5 Eyes intelligence alliance countries have been pushing for an end to end-to-end encryption.
Essentially, end-to-end encryption ensures that messages can only be read in plain text by the sender and the recipient, and not even the messaging service provider can decipher the message.
It provides the most secure form of encryption.
But lawmakers have collectively warned about the severe risks of the availability of strong encryption systems.
In 2018, the 5 Eyes intelligence network released a statement that they will force tech companies to provide encryption backdoors that will enable law enforcers to access content in a readable and usable format.
However, these misguided arguments don’t account for why ordinary citizens use encryption; for financial transactions, private communication, and sharing of sensitive data.

End-to-end encryption ensures that malicious attackers cannot have access to this information. Installing backdoors would essentially eliminate citizens’ access to secure communications.
Nevertheless, interests in eliminating encryption still exist and several nations have made efforts to enforce this violation of privacy.
Recently, the Australian government passed a new law that allows government enforcement agencies to coerce businesses to provide backdoors in their encryption systems and hand over information.
Meanwhile, lawmakers in the US, UK, and Canada have expressed that intention.
Implications of 5 Eyes Alliance on VPN Users
If you thought using a VPN to hide your online activities was enough, think again.
Virtual Private Networks are mostly a preserve of developed countries. This means that most VPN companies are hosted in the US and UK or their top allies where massive surveillance is conducted.
US and UK in particular force VPN service providers to collect and share user data with law enforcement agencies and even though there exist restrictions on which occasions it is applicable, you can’t really put a finger on the extent these laws can reach.
For instance, IPVanish was forced to collect user data for FBI investigations in 2016 despite their no-log policy.
In addition, Lavabit, the private email provider that Edward Snowden used to expose NSA had to shut down when they refused to hand over its data for investigations.
Remember, under the 5 eyes intelligence-sharing agreement, signatories are obligated to share intelligence data with each other. If any nation in the 14 Eyes countries list has access to your online data, it can be shared between them.
It’s, therefore, safe to assume that your online data can fall into the hands of government agents in any country within the alliance.
Meanwhile, if you live in any of the 14 Eyes surveillance countries, you can hardly achieve perfect online anonymity. That’s because every online action you undertake can be recorded and your personal information collected.
The worst part about it is that no one in the general public knows the extent these surveillance systems can go.
What Can You Do to Protect Online Privacy?
While it’s virtually impossible to enjoy 100% anonymity, there are certain measures you can take to get close enough.
Certainly, using a VPN to hide your online activity can help you combat unwarranted surveillance. It does so by encrypting your data and passing it through a secure tunnel which makes it hard for third parties to decipher your traffic.
But don’t expect any type of VPN alone to completely protect you from the 5/9/14 eyes surveillance countries. If you really want to be safe, there are three layers you need to consider when selecting a VPN;
- Your Country’s Laws
- The VPN provider’s business location
- The VPN Server location
Let’s break this down accordingly.
Choose Good VPN Use Locations
First, you should be aware of the online laws and regulations that govern your country.
Online laws are different from one nation to another. Some countries have strict online regulations that violate privacy and hence online activities are monitored closely. China’s social credit system is a good example.
Other nations have reserved online laws. For a start, find out if VPNs are legal in your country.
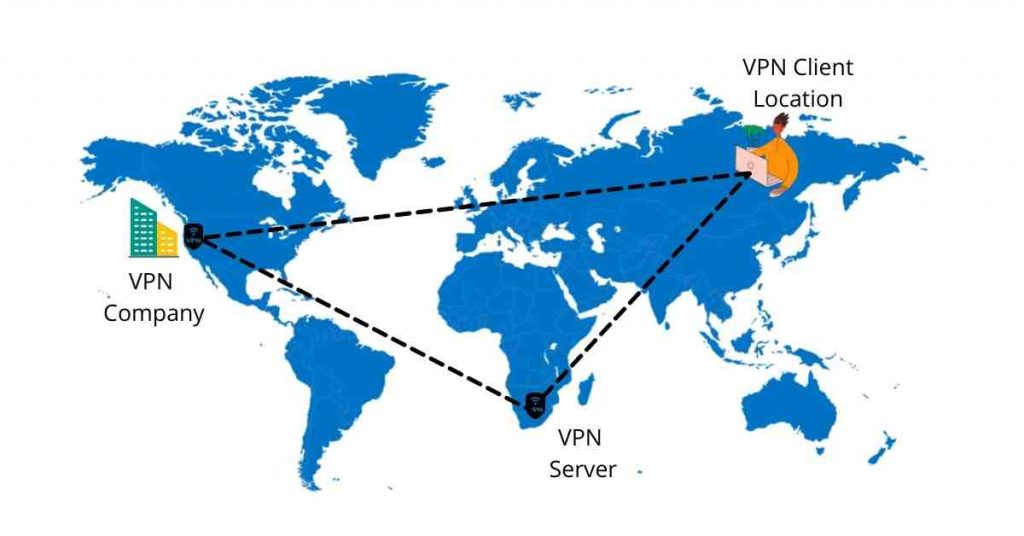
Secondly, where your VPN company is registered matters the most. If the VPN provider is based in a country that’s within the 14 Eyes alliance or a third-party contributor, your online privacy is not guaranteed.
Most of these nations require VPN companies to give law enforcement agencies access to VPN to operate.
Lastly, you also need to check the surveillance laws and practices of the country where the server you choose is located.
This step might seem inconsequential but If you want to be extremely cautious with your online activities, doing due diligence can help you avoid trouble.
Consider No-Log Policies
Then you want to ensure you choose a VPN provider with strict and verified no-logs policies which means they don’t record data of their users’ online activity.
Not every VPN provider that claims to have no-logs policies keeps its promise.
When authorities knock on their doors, some comply and hand over user data. You need to search the internet whether your VPN choice has ever been in such a situation and what action it took.
Using these considerations to pick a VPN eliminates a considerable level of online surveillance. But it won’t be enough.
XKeyscore by NSA has access to almost every internet activity you take no matter your location. Yet that’s just one of the many secretive systems intelligence agencies are using to spy on citizens.
So, you should take more steps to ensure your privacy.
Use Tor Browser
For one, use Tor Browser instead of mainstream internet browsers. Tor is the most advanced and effective online privacy software.
Unlike VPNs which essentially shift trust from your internet service provider to the VPN server, Tor bounces your traffic through three nodes across the internet.

This makes it much more difficult for an eavesdropper to see what you’re doing.
Use Encrypted Platforms
Aside from VPNs, the platforms you use for communication and data transfer also matter a lot.
If you use the normal services by top corporations such as Gmail by Google and Facebook Messenger, you cannot achieve anonymity.
Under the PRISM system, these companies are required to provide access to users’ data for surveillance. Your digital activity will be recorded and shared with intelligence agencies from the 14 eyes intelligence alliance.
To protect your privacy further, use applications that offer strong end-to-end encryption which makes it hard for surveillance agencies to intercept and decipher your data.
For instance, you can use either Wire or Signal which offer more secure communication than WhatsApp and Facebook Messenger.
ProtonMail can replace Gmail for your emailing activities as it has zero access encryption and its parent company is based in Switzerland which is not a signatory to any surveillance agreements.
Conclusion
Privacy is about autonomy.
You choose what you want to keep private and what you can share publicly.
Understanding that anything shared on the internet can be accessed hence it stops being private, should be the guiding principle in your online activities.
Whether you are a citizen of the 14 Eyes, 9 Eyes, 5 Eyes member countries, and their compatriots, or not, your online privacy is almost uncertain.
The technological advancement intelligence agencies have made to enable citizen surveillance and the constant push by lawmakers across the world to limit online privacy should wake you up.
It’s very likely that most governments will continue to do more surveillance in the name of ensuring the security of their citizens.
Consequently, citizens will struggle to access secure channels of communication, a major threat to digital freedom.
The solutions we’ve covered should help you achieve considerable privacy for now.


